Solutions Summary - Matter
The proliferation of smart devices has brought convenience to our lives but also a critical challenge: security. Imagine a refrigerator, thermostat, or lightbulb becoming an entry point for cyberattacks. This is where Matter comes in. Matter aims to ensure secure communication and interoperability between different smart home devices from various manufacturers.
With PKI at its core, Matter creates a secure foundation for the smart home. By ensuring every device is authenticated, communication is encrypted, and updates are verified.
As a product vendor manufacturing Matter-compliant devices in the Matter IoT ecosystem, you need a PKI to issue device certificates. In the Matter IoT specification, certificates are used to implement unique identities to ensure that only authenticated and certified devices can join the network.
The Matter specification is available on the Connectivity Standards Alliance website, and a Matter-compliant PKI must follow the Matter PKI Certificate Policy.
What is Matter
Matter aims to build a universal IPv6-based communication protocol for smart home devices. The protocol defines the application layer deployed on devices and different link layers to help maintain interoperability.
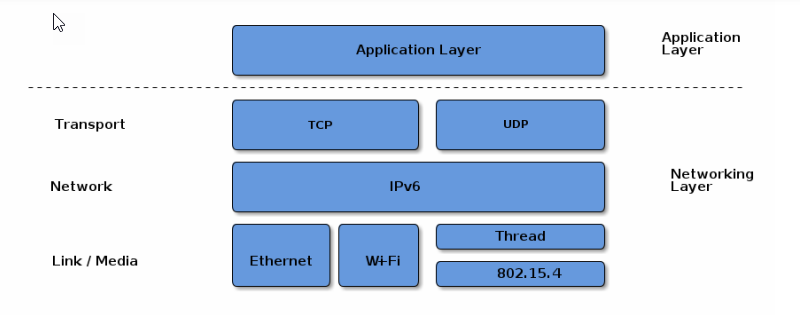
Matter Application and Network Stack
All unicast Node-to-Node messages are secured and authenticated and provide replay protection. Building on top of IPv6 multicast. Matter also includes group messaging facilities useful for efficiently addressing an LLN. The group messaging features prioritize low latency of packet processing.
Matter Security Overview
Key Security Features:
X.509 certificates: These digital certificates verify devices' identities and establish trust.
Elliptic Curve Cryptography (ECC) is a strong form of public-key cryptography. It's particularly well-suited for IoT devices with constrained resources because it offers comparable security to traditional methods like RSA but with smaller key sizes. This efficiency translates to lower computational overhead and reduced energy consumption, crucial factors for resource-limited devices..
AES encryption: A widely used encryption standard for securing data exchanged between devices.
SPAKE2+: A secure method for devices to authenticate each other, even when using simple passcodes.
Device Attestation: Each device has a unique identity verified by the manufacturer and the Connectivity Standards Alliance (CSA), ensuring authenticity.
Operational Credentials: When a device joins a Matter network, it receives unique credentials, like a temporary access pass, allowing it to operate securely within that network.
Distributed Compliance Ledger (DCL): A shared record of approved devices and their certificates, helping to maintain trust and security across the ecosystem.
Matter Security using X.509 Certificates - why this matters!
Matter employs the well-established X.509 certificate format for its security measures.
During manufacturing, each device is assigned an initial X.509 certificate that cannot be changed or modified afterward. This immutable certificate serves as a unique and permanent identifier for the device, crucial for establishing trust and secure communication within the Matter ecosystem.
DAC delivered and injected by the OEM from its own PKI (PAA-PAIs)
Matter enforces secure over-the-air (OTA) FW/SW updates
Practical implementation not specified
Secure boot is not yet mandatory, but highly recommended
Device Attestation Certificate Issuance Model
Here's how Matter's Device Attestation Certificate issuance maps to the familiar X.509 issuance model.
Product Attestation Authority (PAA): a root Certificate Authority and the Matter root identity of a Vendor. The PAA X.509 certificate is self-signed, inherently trusted, associated with a VendorID, and must be registered into the DCL. The PAA certificate signs PAIs.
Product Attestation Intermediate (PAI): a subordinate Certificate Authority and the Matter identity of a specific product reference manufactured by a Vendor. PAI X.509 certificates are issued by the PAA and associated with ProductIDs. The PAI signs DACs.
Device Attestation Certificate (DAC): an end-entity X.509 certificate and the Matter unique, immutable identity of a device manufactured by a Vendor. A DAC is issued by a PAI certificate authority and injected into the device at manufacturing and is, as such, associated with a ProductID. The DAC can be seen as the initial device certificate proving the genuineness of a Matter device from a given approved Vendor.
Example Use-cases
1. Silicon vendor hosts PAIs and injects device attestation certificates onto chips.
This use-case describes how Matter device attestation certificates are created and installed on devices, involving the silicon vendor (chip manufacturer) and the OEM (Original Equipment Manufacturer, the company making the final product).
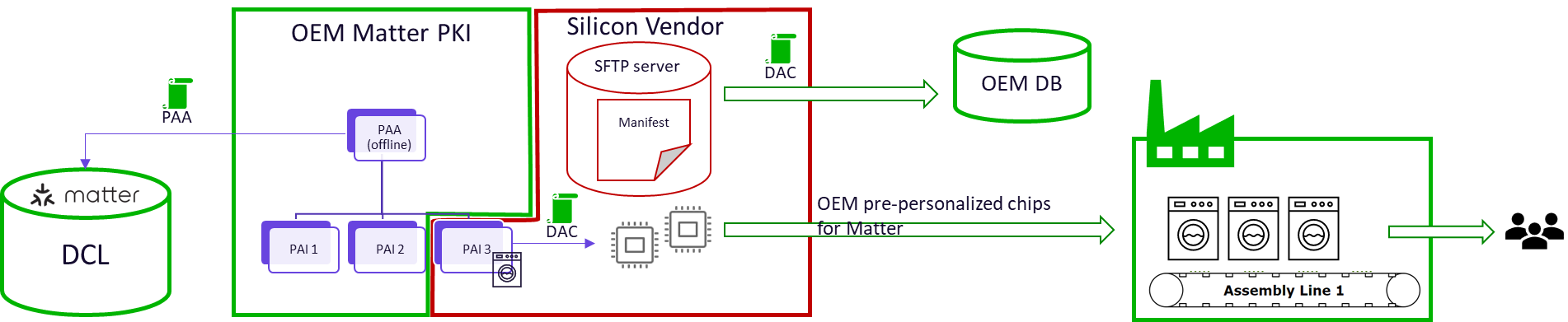
The silicon vendor physically puts the DACs onto the chips during manufacturing.
The OEM establishes its root of trust, the PAA (Product Attestation Authority).
Silicon vendor creates as many PAIs as needed for the OEM
Silicon vendor creates unique identifiers for the chips destined for the OEM's specific products
Finally, the OEM places orders for the microcontrollers (MCUs), the chips containing the pre-installed DACs, according to their individual product needs.
2. DACs are injected after manufacturing
This solution provides a streamlined and secure approach to device identity in Matter. The process simplifies chip procurement and enhances security by generating unique digital fingerprints directly on blank microcontrollers (MCUs) during manufacturing.
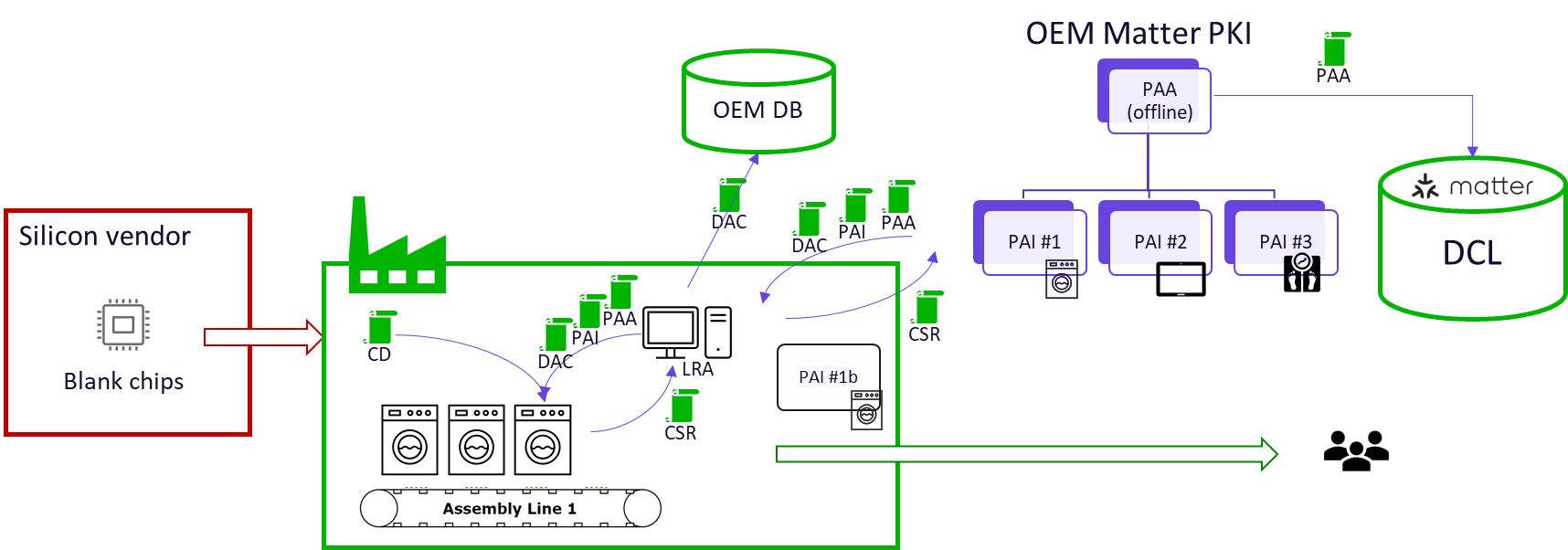
OEM sets-up centralized Matter PKI with optional back-up local PAI (PAI #1b)
OEM purchases generic blank MCUs
At manufacturing, DAC private key and CSR are generated on the device
LRA (Local Registration Authority) forwards CSR to PAI for signing and collects DAC in return
DAC is injected into the device
3. DACs are injected after manufacturing
This diagram shows a system where device security is finalized after manufacturing, giving the OEM strong control and flexibility. Here's the flow:
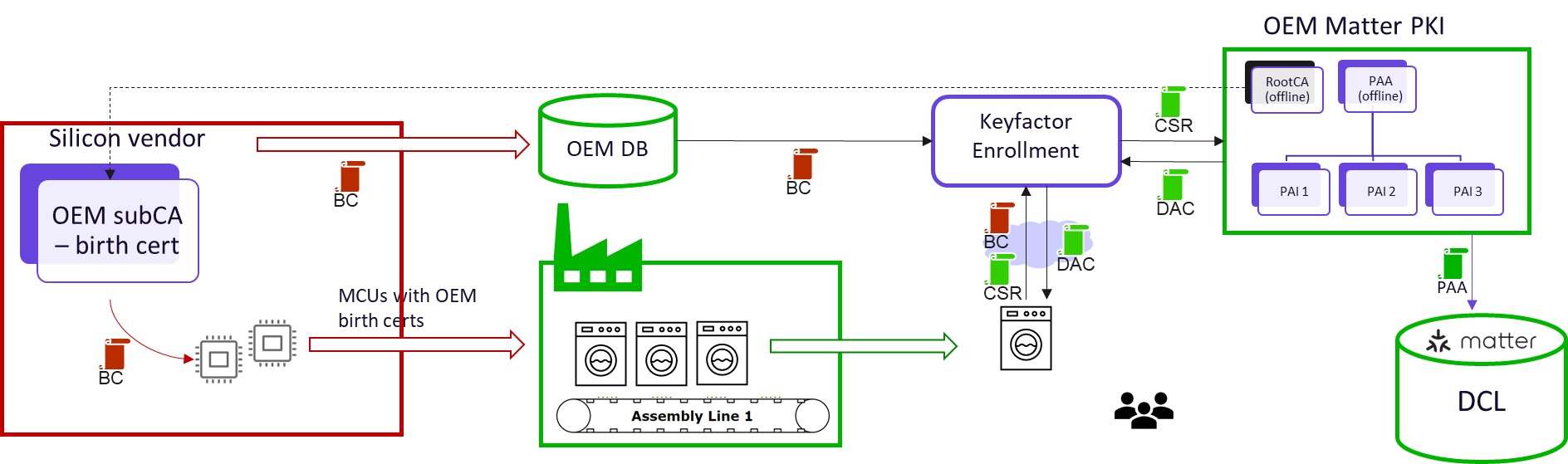
OEM sets up centralized Matter PKI and a separate root for birth certs
Silicon vendor creates issuing CA for OEM birth certificates and creates OEM part number
OEM purchases MCUs with generic OEM birth certs and manufactures the device
When the device arrives at the customer, the OEM app finishes provisioning:
The device generates DAC private key and CSR and uses a birth certificate as proof of ID
The enrollment server vets the device and forwards CSR to PKI, injects DAC
Device is Matter-ready.
Conclusion
Matter device attestation relies on robust PKI implementation offered by EJBCA to guarantee the integrity and security of IoT ecosystems. By utilizing a hierarchical certificate structure, with the PAA as the root of trust, PAI for product lines, and unique DACs for each device, Matter ensures that only authorized devices connect to the network.
EJBCA facilitates this process by providing the tools to manage and automate the entire certificate lifecycle, from issuance and revocation to renewal. This is crucial for Matter's attestation models, whether it's:
Compliant with Matter security requirements
Compliant with worldwide data protection regulations
Flexible deployment options: hardware, software, cloud, SaaS
Easily extensible
By leveraging EJBCA, manufacturers can establish a robust and scalable PKI infrastructure for Matter-compliant device attestation. This ensures the authenticity and integrity of devices to a secure smart home ecosystem."
