Solution Summary - Secure Contract Manufacturing
When creating device identities in-situ, it is important that sensitive information is not leaked and copied by a rogue player inside of the manufacturing environment. For Contract Manufacturers (CM), depending on the country in which the CM resides, there are regulations that prevent access to key material outside of that country. Here are lists of challenges and mitigations in securing a manufacturing environment:
Challenges:
How to get a unique device identity for devices in a contract manufacturing environment
Prevent interception of key material during manufacturing process
Prevent exposing company PKI issuing certificate authorities
Entropy (randomness) on devices may be poor.
CM overproduces and makes counterfeit parts
Dealing with regulatory requirements (e.g., China CM can’t connect to EMEA or US PKI)
If the contract with the CM expires, how to prevent continued device generation
Mitigations:
Use x.509 certificates from a private PKI to attest to a unique device identity.
Standards like WiSUN, IEEE 802.1AR, and Matter require a PKI
Generate keypairs on devices and use a certificate signing request to ask for certificate.
Allow access to a good source of entropy for constrained devices
Utilize a PKI that can count the number of certificates issued
Place a managed portion of the PKI into a secure hardware appliance living in the manufacturing facility
Allows remote turning off the issuing authority
Since the issuing authority is in the country where the signing keys exist, can import into China
Provides a good source of entropy
Limits the exposure footprint of the PKI
Eliminates the need for a continual internet connection
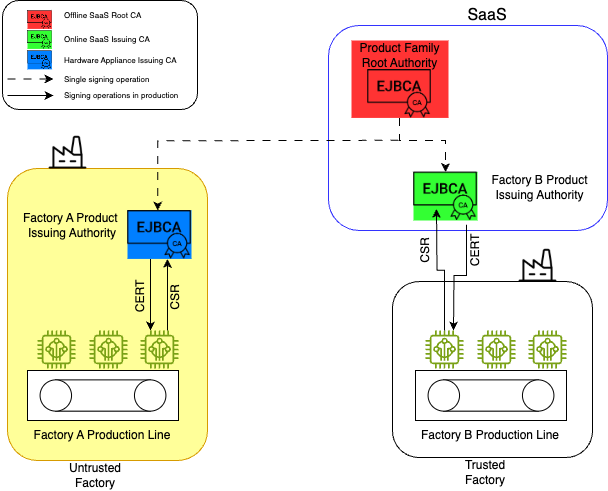
Example EJBCA setup for trusted and untrusted manufacturing sites
EJBCA is a highly configurable and hybrid approach to standing up a robust PKI suitable for both trusted and untrusted manufacturing sites.
EJBCA can issue fully compliant x.509 based certificates for:
Matter
WiSUN
IEEE 802.1AR
3GPP
In addition to x.509 certificates, EJBCA is capable of issuing other IoT use case certificates:
Card Verifiable Certificates (CVC)
SSH Certificates
Other challenges in securing manufacturing environments
Besides device identities, there are other risks encountered when dealing with manufacturing environments. Here is a list of those challenges and their associated mitigation:
Challenges:
Customizing identities (like serial numbers) from a database
Provisioning symmetric keys for other use cases (KMS Integration)
Preventing firmware theft or modification
Mitigations:
Have a hardware based secure firmware repository on the factory floor
Allow only an authorized hardware device to connect to the:
PKI
KMS
Databases
Generate secrets in a secure hardware box if the device cannot do it
Customize the CSR’s identity information based on a secure database connection
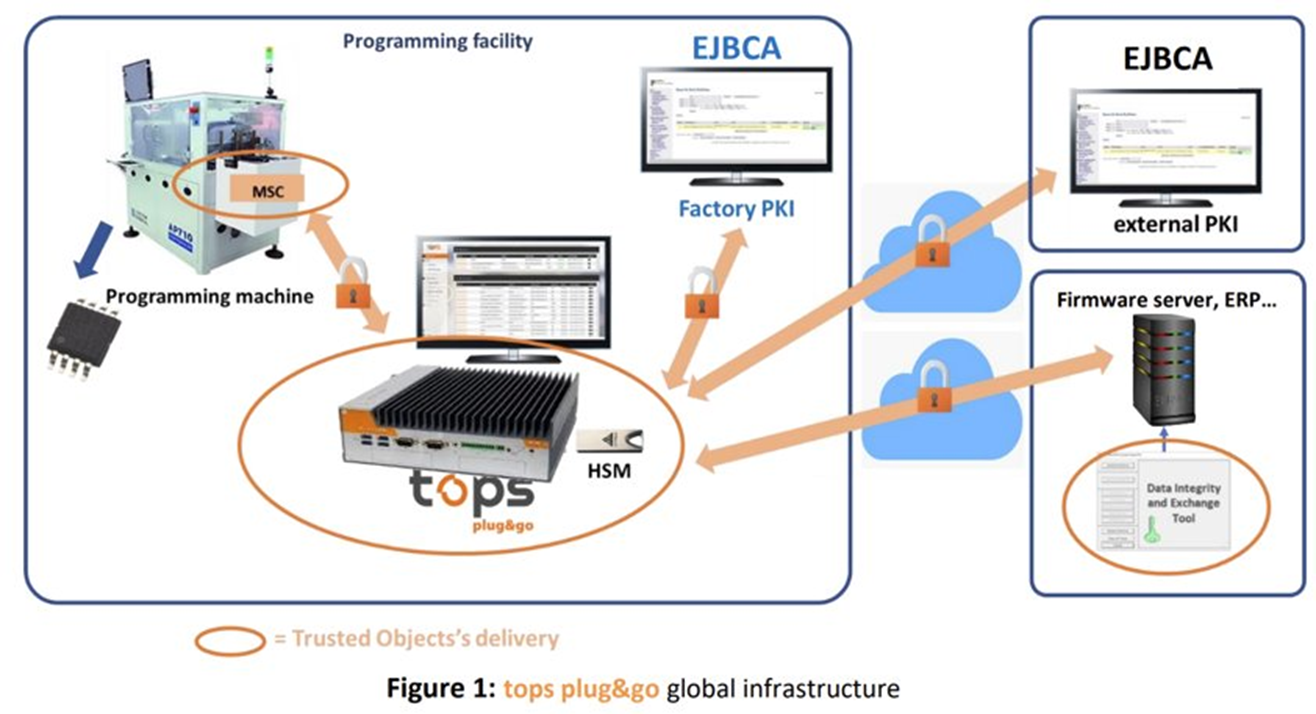
Adding TOPS to an EJBCA deployment
Keyfactor and Trusted Objects have a tight integration to solve these additional challenges. The Trusted Objects TOPS (Trusted Objects Platform Security) solution has the following features:
The TOPS box is a secure, factory floor hardened device only accessible by the device manufacturer and not the contract manufacturer.
Includes a Hardware Security Module (HSM) FIPS 140-2 Level 3 to perform cryptographic operations and secure private keys.
Encrypted SSD storage
Robust production control with counters and reports
Can create an internal robust source of entropy (randomness)
Securely create keys on behalf of the devices
Customize and sign the CSR on behalf of the device with data from an external database
The TOPS box can be whitelisted to allow access to one or more of the following:
The EJBCA on-premises Issuing CA for device identities
The EJBCA cloud-based Issuing CA for device identities
An external Key Management System (KMS) for creation and provisioning of symmetric keys
A device or a device programming machine
An external database or MRP/ERP system
An external firmware repository so that only known firmware is provisioned
In addition, the TOPS box can host an EJBCA instance inside of it, forgoing the requirement to have an EJBCA hardware appliance provisioned in the CMs datacenter.
Example EJBCA plus TOPS integration in securing a manufacturing environment
Key Takeaways
Securing a manufacturing environment introduces various security challenges such as:
Transparency and Trust are key to protecting against intellectual property theft.
Unique, trusted, and secure device identities are required to identify legitimate devices.
Sometimes integrating with MRP systems for serial numbers is important if UKID chips are not utilized.
Assuring only valid firmware is loaded onto a device and that the firmware is not compromised or stolen.
Trusted and secure symmetric key provisioning is required to prevent tampering.
Robust reporting and securely connecting to OEM databases or MRP/ERP system is important.
A private and hybrid PKI model like the one provided by EJBCA coupled with the additional capabilities of TOPS can easily meet all of these challenges in a fully scalable, secure, and controllable manner.