Solution Summary - ISO-15118
ISO-15118 Overview
As Electric Vehicle (EV) popularity increases, the demand for privately run charging ecosystems continues to rise. EVs can be charged at home by hooking up to the power grid via a wall-mounted charger. However, this limits the vehicle’s range. To create a viable Internal Combustion Engine (ICE) alternative, a network of privately owned and operated public charging stations are required.
The Electric Vehicle Charging Controller (EVCC) must communication to the charging station or Supply Equipment Charging Controller (SECC). This communication keeps track of the vehicle’s battery charging cycle to prevent overcharging or other unintended mis-behaviors. The standardization of the communications for transferring information between the SECC (charging equipment) and EVCC (electric vehicle) is what the ISO 15118 series defines.
The ISO 15118 series defines the communications between the vehicle and charger, optimizing battery charging in both energy and cost. It also addresses a means to create a convenient billing system for public charging. With Plug and Charge (PnC), the vehicle has a contract with an energy supplier. Whenever the vehicle uses a public charger, the owner is automatically billed. The entity a vehicle owner has a contract with is known as an Electric Mobility Service Provider (eMSP) or Mobility Operator (MO).
ISO 15118 also realizes that the charging operation can be a means of ingress into the vehicle. In particular, a means to bypass vehicle security. For home wall chargers, the homeowner trusts the charging station. However, public charging stations could be used for nefarious means. Therefore, the ISO 15118 series establishes a means to establish trust between the vehicle and the charging station.
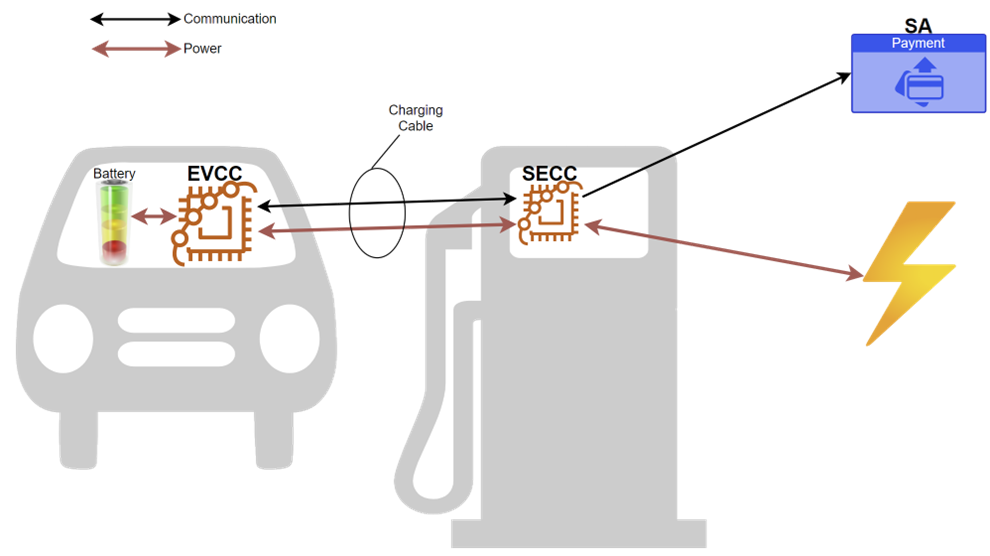
ISO 15118 Defines Communication between the EV and the Charger
ISO 15118-2
ISO 15118-2 was released in 2014 and defines the communication protocol for:
One-way power flow (Charging Station to Vehicle) charging methods
Establishing a means for a vehicle to trust a charging station.
A method to communicate power consumption from the charging station to the vehicle in a trusted manner.
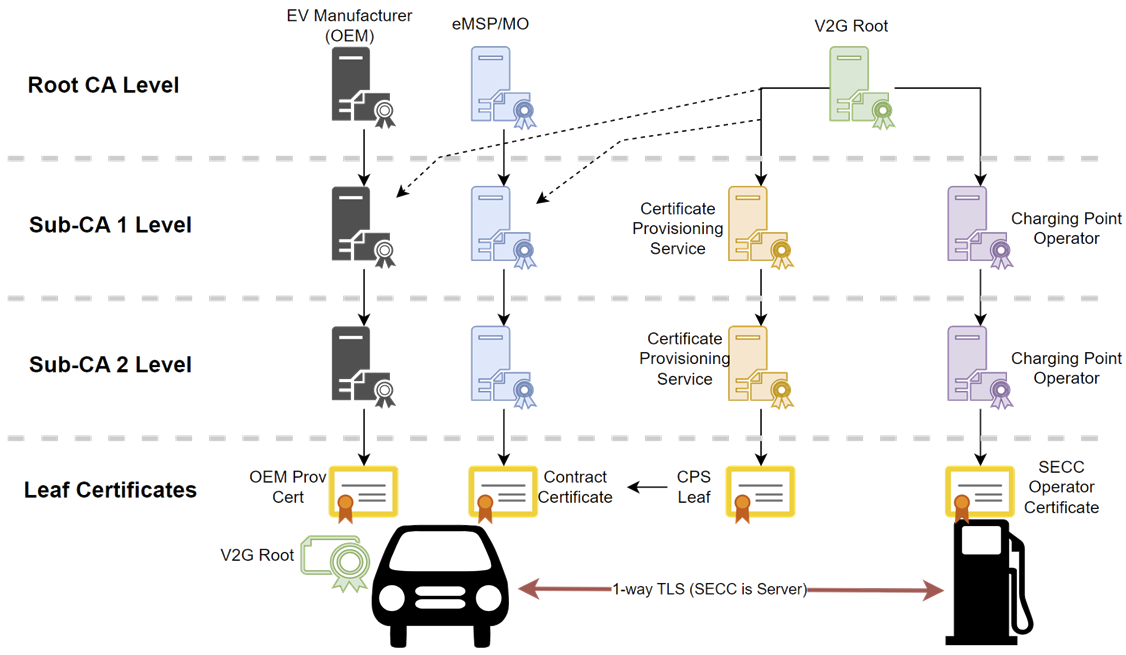
Example ISO 15118-2 PKI
NOTE: V2G Root Establishes Global Trust
Key Elements in ISO 15118-2
OEM Prov Cert: Vehicle manufacturer certificate, unique to each vehicle, used to create a Contract Certificate between the vehicle owner and the eMSP.
Contract Certificate: A certificate used in signing receipts from a charging operation. Used in billing operations with the eMSP.
CPS Leaf: A certificate used to deliver the contract certificate to the vehicle. Used in establishing the contract between the eMSP and EV owner. Also used in certificate/contract updates.
SECC Operator Certificate: A certificate, provisioned by the charging station owner, that proves the authenticity of a public charging station.
V2G Root: This is the ultimate Trust for the ecosystem. If anything chains to this trust, the entire ecosystem believes in its authenticity. These roots, therefore, are run by very closely audited bodies & must have very strict standards for issuing certificates.
ISO 15118-20
ISO 15118-20 was released in 2022 and expands the work performed in ISO 15118-2 by:
Defining improved charging methods to reduce charging efforts
Adds functionality for power flow from the Vehicle to a Charging Station (this makes the vehicle’s batteries a source of grid energy to optimize efficiencies in the grid).
Establishes a more robust security ecosystem by:
Updating security protocols
Add a Vehicle Identity Certificate to create mutual trust between the vehicle and the charging station, thus preventing attacks on the charging infrastructure.
Allowing for the addition and removal of more ecosystem trust anchors between the vehicle to grid.(V2G roots)
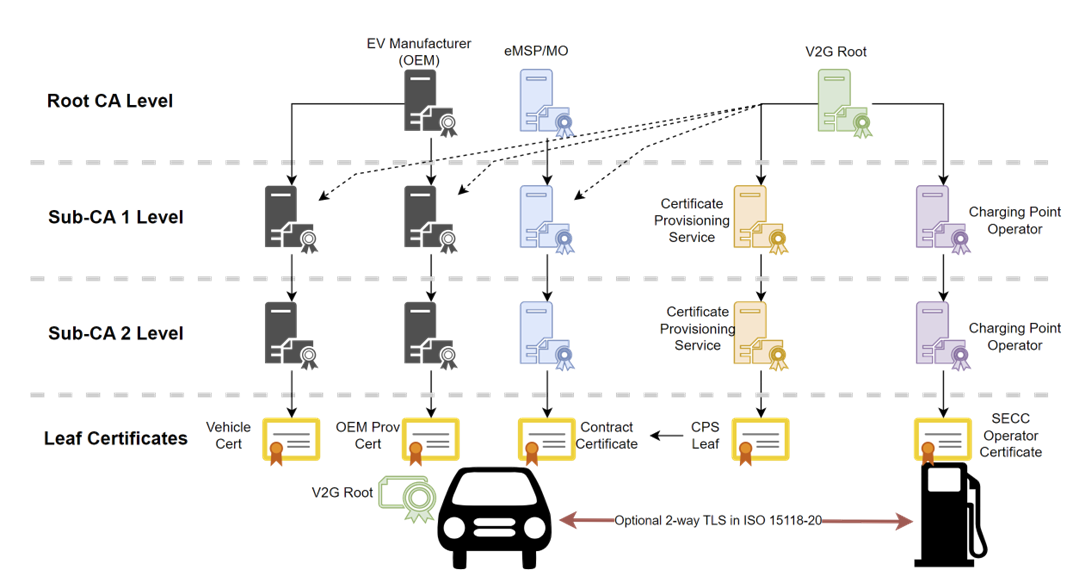
Example ISO 15118-20 PKI
NOTE: V2G Root Establishes Global Trust
Key Elements in ISO 15118-20
All of the key elements defined in ISO 15118-2 are used in ISO 15118-20.
Vehicle Certificate: Vehicle manufacturer certificate, unique to each vehicle, used to authenticate a vehicle to a charging station. This certificate is used to prevent an attack on the charging station, the billing system, and the supply infrastructure.
Example Threats to EV Charging
Pirate Charging Stations: A nefarious actor could set up fake charging stations in an attempt to steal contract data from an EV. To prevent this, a PKI provides a way to prove that the charging station comes from a valid charging station operator.
Replaying receipt data: To prevent a bad actor from trying to charge a consumer multiple times for the same transaction, a unique transaction identifier is placed on the receipt. The receipt is then encrypted by the contract certificate. In this way, the charging station cannot see the details of the receipt, and cannot spoof one. A contract certificate PKI provides a means to provision the Contract Certificate so that the charging station does not require this certificate for validation.
Stolen EV or EVCC: If an EV or its charging controller is stolen, the revocation function of a PKI is used. The EVs certificates, once revoked, are no longer trusted and cannot be used in further transactions. This limits a stolen EVs usage.
Stolen Charging Station: Similarly, if a charging station is stolen, a robust PKI can revoke the charging stations’ leaf certificate (SECC Operator Certificate). In this manner, the charging station is rendered useless.
Nefarious Charge Point Operator: If a charging station operator (eMSP/MNO) tries to simulate a fake charging transaction, the ISO 15118 PKI structure prevents this from happening. To prevent this attack, the signed and encrypted data for the receipt is sent to the Charging Station. The encryption/signature is provided by the private contract key kept in the EV. Therefore, the Charging Station can never simulate a new transaction.
Hacking an EV: The EVCC will only trust communications that come from the V2G root ecosystem. This combats the chances that the EVCC will trust a hacker’s connection.
Hacking a Charging Station: In ISO 15118-20, the SECC should trust the vehicle. This combats the chances that the charging station (SECC) will trust a hacker’s connection.
Who to the trust in ISO 15118
As of now, there are three official V2G Root certificate authorities (CAs) in the ISO 15118 ecosystem. These organizations are highly audited and must have very robust vetting mechanisms to approve the issuance of certificates into the ecosystem. Therefore, there are only a few official V2G root CAs in the ISO 15118 ecosystem. The three recognized V2G Roots are:
Hubject – One of the most prominent V2G Root CAs, especially in Europe and North America, providing secure PKI infrastructure for vehicle-to-grid communications.
Gireve – A French company providing services for EV interoperability and secure communications. Gireve operates a V2G Root in the ISO 15118 ecosystem.
Nuvve – Nuvve operates within the V2G space and is involved in providing solutions for grid management.
ISO 15118 Limitations
As robust as the ISO 15118 series is, there are still some items not addressed in this ecosystem:
Governance requirements: How many & who controls the V2G roots? While the standard outlines the communications, it doesn’t outline the auditing and vetting protocols used for the V2G Root operators.
Certificate Rotation Mechanism: Maintaining active certificates is left to the OEM, eMSP, and Charge Station Operators. The standard does not outline how this should take place. If a certificate is issued in an unsafe manner, then the trust in the OEM, eMSP, or Charge Station Operator is compromised.
Updating V2G roots on EVCC and SECC: When a V2G root is updated or expires, the mechanism to handle this update is not defined. That is, pushing newly trusted V2G roots is mentioned, but a mechanism to do this is not defined.
Multiple Contract Certificates: ISO 15118-2 does not allow for more than one contract certificate per vehicle. This is addressed by ISO 15118-20; however, this standard is not currently adopted industry wide.
Multiple algorithm support: ISO 15118-2 defines ECC secp256r1 as the only accepted algorithm. ISO 15118-20 defines ECC secp521r1 and ED448 Goldilocks Curve as the acceptable curves. To maintain backward compatibility, this means that all three curves must be supported. Therefore, OEMs, eMSPs, and Charging Station Operators must maintain three PKIs.
Support of ED 448: The standard requires that all cryptographic operations happen within a Hardware Security Module (HSM) in the PKI ecosystem. As of this writing, there are no HSM manufacturers that support ED448. Standards like CharIN V2G eliminate this concern by only issuing ECC secp521r1 certificates. CharIN is ISO 15118-20 compatible, but eliminates the ED 448 curve requirements.
Mutual trust: ISO 15118-2 only supports a vehicle trusting the charging station. ISO 15118-20 supports mutual trust (mTLS). For complete backwards compatibility, this means that mTLS is only optional in charging stations.
Conclusion
Creating policies and procedures that leverage state-of-the-art PKI software along with state of the art cryptography hardware support the ISO 15118 security posture. That security posture, when properly sponsored, documented, maintained, and audited can be used to support the argument that a player in the EV charging ecosystem is ISO 15118 compliant.
Keyfactor’s EJBCA software streamlines implementing these policies and procedures with a robust set of configurations, scalability, audit logging, security mechanisms, and hardware integrations; this makes EJBCA a perfect solution for small to large vehicle manufacturers (OEM), charging station operators, and eMSP providers.
When it comes to unplanned downtime prevention, adding Keyfactor’s Command for IoT brings additional functionality that goes beyond a PKI. Managing device certificate rotation, pushing new roots of trust to a device, centralizing device revocation, and full scalability are supported.
Overall, players in the ISO 15118 ecosystem need to meet existing regulations when it comes to cybersecurity and charging electric vehicles. A robust solution relies on structured policies and procedures. Keyfactor has partnered with many Fortune 100 companies to do this in the Enterprise space, and has products to assist the requirements in the ISO 15118 ecosystem, too.
